Software supply chain security remains a challenge for most enterprises

Software supply chain security remains a significant challenge for enterprises, with the recent Log4j vulnerability bringing attention to the issue. While awareness of the importance of a secure software supply chain is high, implementing effective strategies is a struggle for many technology executives.

Courtesy Photo
Log4j, perhaps more than any other security issue in recent years, has thrown the spotlight on software supply chain security, with even the White House weighing in. Even though almost every technology executive is aware of the importance of developing a trustworthy and secure software supply chain, most are unsure how to best implement a strategy around it.
The number of CVEs (Common Vulnerabilities and Exposures) continues to rise steadily, and there isn’t a single container that doesn’t contain at least some vulnerabilities. Some of these may be in libraries that aren’t even used when the container is running, but they are still vulnerabilities.
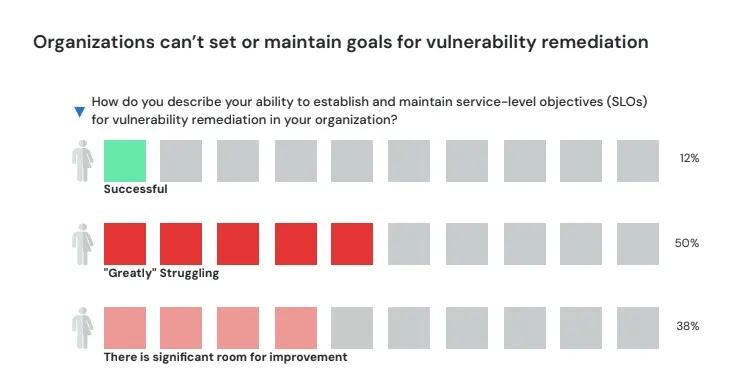
Image Credits: Slim.ai
According to Slim.ai’s most recent Container Report, the average organization now deploys more than 50 containers from their vendors each month (with nearly 10% deploying more than 250). However, only 12% of security leaders polled by Slim.ai said they were able to meet their own vulnerability remediation targets. Everyone else says they are “greatly” struggling or see significant room for improvement. While those organizations are all putting pressure on their vendors to improve their security posture and deliver, vendors and buyers frequently can’t agree on which CVEs require patching in a container.
According to Ayse Kaya, Slim.ai’s VP of Strategic Insights and Analytics, the interaction between buyers and vendors is still often driven by spreadsheet exchanges and ad hoc meetings between security groups. According to the company’s report, which was created in collaboration with research firm Enterprise Strategy Group, 75% of organizations still exchange information with their vendors in this manner, even though nearly all security leaders (84%) would like to see a centralized collaboration platform for managing vulnerabilities. For the time being, however, it appears that emailing spreadsheets back and forth is still the norm.
All of this will inevitably result in inefficiencies. Most organizations that responded to the survey said they employ six or more vulnerability remediation specialists (with a quarter employing more than ten). One of the industry’s major issues is that more than 40% of the alerts these teams receive are false positives — frequently for libraries that are part of a container but aren’t used in production. As a result, Kaya, for example, strongly advocates for creating minimal container images. One could argue that this should be a best practice in any case, because it reduces false positives and creates a smaller attack surface.
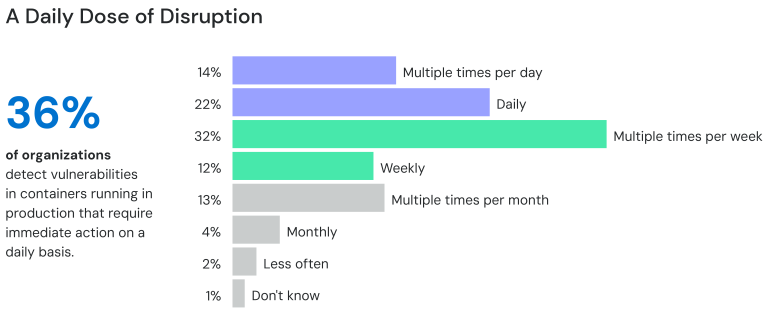
Image Credits: Slim.ai
All of this inevitably leads to inefficiencies. The survey found that most organizations employ six or more vulnerability remediation specialists (with a quarter employing more than ten). One of the major issues in the industry is that more than 40% of the alerts received by these teams are false positives, often for libraries that are part of a container but aren’t used in production. As a result, Kaya, for example, strongly advocates for the creation of minimal container images. One could argue that this should be a best practice in any case because it reduces false positives and creates a smaller attack surface.
Of course, these vulnerabilities must be addressed by more than just security teams. All these efforts, however, slow down the overall development process. Most businesses experience some disruptions multiple times per week, for example, when a vulnerability in a production container is discovered. According to Slim. Ai’s report, the average container now sees a new release every 11 days and is affected by 311 CVEs (up from 282 in 2022). All of this means more work, more interruptions, and more time spent working with vendors to resolve issues.







